When browsing the web or building websites, you may encounter numbers like 404, 500, or 301. These numbers are HTTP status codes — short messages from a web server that tell your browser whether a request succeeded, failed, or needs more action.
This guide covers all major HTTP status codes, including informational, success, redirection, client errors, and server errors.
1. What Are HTTP Status Codes?
HTTP status codes are standardized responses from a web server when a browser or client requests a resource.
Each status code is three digits, and the first digit defines the response category:
- 1xx – Informational responses
- 2xx – Success responses
- 3xx – Redirection messages
- 4xx – Client error messages
- 5xx – Server error messages
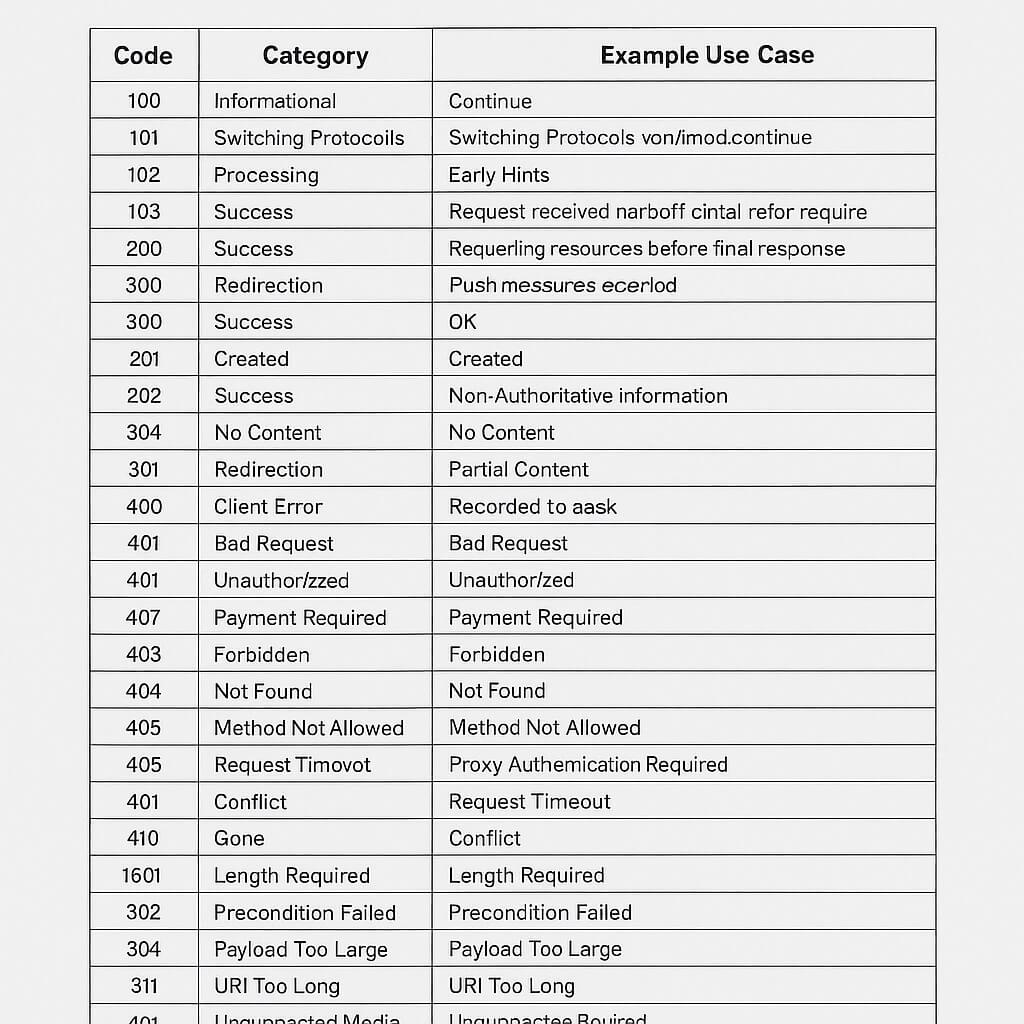
2. Complete HTTP Status Code Table
| Code | Category | Meaning | Example Use Case |
|---|---|---|---|
| 100 | Informational | Continue | Request received, client should continue |
| 101 | Informational | Switching Protocols | Server is switching protocols |
| 102 | Informational | Processing | WebDAV request still in process |
| 103 | Informational | Early Hints | Preloading resources before final response |
| 200 | Success | OK | Request succeeded (normal webpage load) |
| 201 | Success | Created | Resource successfully created |
| 202 | Success | Accepted | Request accepted but processing later |
| 203 | Success | Non-Authoritative Information | Metadata from another source |
| 204 | Success | No Content | Request succeeded, no content returned |
| 205 | Success | Reset Content | Client should reset form input |
| 206 | Success | Partial Content | Partial resource returned (range request) |
| 300 | Redirection | Multiple Choices | Multiple options for resource |
| 301 | Redirection | Moved Permanently | Resource moved to a new URL |
| 302 | Redirection | Found | Temporary redirect |
| 303 | Redirection | See Other | Redirect to a different resource |
| 304 | Redirection | Not Modified | Cached version is still valid |
| 307 | Redirection | Temporary Redirect | Same method redirect |
| 308 | Redirection | Permanent Redirect | Method preserved permanent redirect |
| 400 | Client Error | Bad Request | Invalid syntax in request |
| 401 | Client Error | Unauthorized | Authentication required |
| 402 | Client Error | Payment Required | Reserved for future use |
| 403 | Client Error | Forbidden | Access denied |
| 404 | Client Error | Not Found | Resource not found |
| 405 | Client Error | Method Not Allowed | HTTP method not supported |
| 406 | Client Error | Not Acceptable | Resource not available in acceptable format |
| 407 | Client Error | Proxy Authentication Required | Must authenticate with proxy |
| 408 | Client Error | Request Timeout | Server timed out waiting for request |
| 409 | Client Error | Conflict | Request conflicts with server state |
| 410 | Client Error | Gone | Resource permanently removed |
| 411 | Client Error | Length Required | Content-Length header missing |
| 412 | Client Error | Precondition Failed | Server precondition failed |
| 413 | Client Error | Payload Too Large | Request body too large |
| 414 | Client Error | URI Too Long | Request URL too long |
| 415 | Client Error | Unsupported Media Type | Format not supported |
| 416 | Client Error | Range Not Satisfiable | Invalid range request |
| 417 | Client Error | Expectation Failed | Expect header not met |
| 418 | Client Error | I’m a Teapot | Joke status from RFC 2324 |
| 422 | Client Error | Unprocessable Entity | WebDAV request validation failed |
| 425 | Client Error | Too Early | Request too early to process |
| 426 | Client Error | Upgrade Required | Switch to a different protocol |
| 428 | Client Error | Precondition Required | Missing required conditions |
| 429 | Client Error | Too Many Requests | Rate-limiting triggered |
| 431 | Client Error | Request Header Fields Too Large | Headers too large |
| 451 | Client Error | Unavailable For Legal Reasons | Blocked due to legal demand |
| 500 | Server Error | Internal Server Error | Generic server failure |
| 501 | Server Error | Not Implemented | Functionality not supported |
| 502 | Server Error | Bad Gateway | Invalid response from upstream server |
| 503 | Server Error | Service Unavailable | Server temporarily overloaded |
| 504 | Server Error | Gateway Timeout | Upstream server timeout |
| 505 | Server Error | HTTP Version Not Supported | Unsupported HTTP version |
| 506 | Server Error | Variant Also Negotiates | Internal negotiation error |
| 507 | Server Error | Insufficient Storage | WebDAV storage full |
| 508 | Server Error | Loop Detected | Infinite loop detected |
| 510 | Server Error | Not Extended | Missing policy extensions |
| 511 | Server Error | Network Authentication Required | Authenticate to access network |
3. Common HTTP Error Codes & Fixes
404 Not Found
- Cause: The requested page doesn’t exist.
- Fix: Check URL spelling or update broken links.
500 Internal Server Error
- Cause: Generic server issue.
- Fix: Check server logs for PHP or database errors.
503 Service Unavailable
- Cause: Server is overloaded or down for maintenance.
- Fix: Reduce traffic load or wait for maintenance to finish.
4. Summary
HTTP status codes are essential for understanding web server responses. Knowing them helps developers debug issues faster and optimize website performance.